What is a ‘stealth’ VPN?
A stealth VPN, put simply, is a VPN that hides the fact that it is a VPN when it is used. Stealth VPNs are the next level of Internet secrecy and are extremely useful when it comes to bypassing network firewalls, evading government censorship, and more.
Learn more about stealth VPNs, how they work, and how to select one that’s right for you.
Why You Might Use a Stealth VPN
VPNs work by encrypting your Internet traffic, preventing your ISP and the websites you visit from being able to identify you. This allows you to go online without revealing your identity, an important tool for staying safe.
However, firewall technologies have become increasingly sophisticated since the advent of VPNs. Many firewalls can detect if you’re using a VPN by analyzing the data packets from your device since encrypted data from ordinary VPNs is distinct from unencrypted data. They then block the VPN traffic.
VPNs may be blocked by your network or ISP for a number of reasons. If you’re using a school or business network, your administrator may block VPNs to prevent you from accessing irrelevant or objectionable content when you are expected to be working.
Some ISPs may block or throttle VPN usage in order to maintain fair bandwidth access. For example, some ISPs throttle users who excessively use streaming services or file-sharing programs. Some users will try to get around this using VPNs, so ISPs will throttle VPN traffic to enforce their policies.
Additionally, streaming services such as Netflix will often block VPNs in order to maintain regional blocks on certain types of content. This is because users will often use VPNs to access movies and TV shows that are ordinarily inaccessible in their countries.
More worryingly, some countries that engage in Internet censorship use a method called deep packet inspection to monitor network traffic. Deep packet inspection is a data processing method used to analyze network data requests in detail and block censored websites and content.
If you are using an ordinary VPN in a country known for Internet censorship, you risk detection due to deep packet inspection, as government firewalls will be able to easily identify your encrypted data requests.
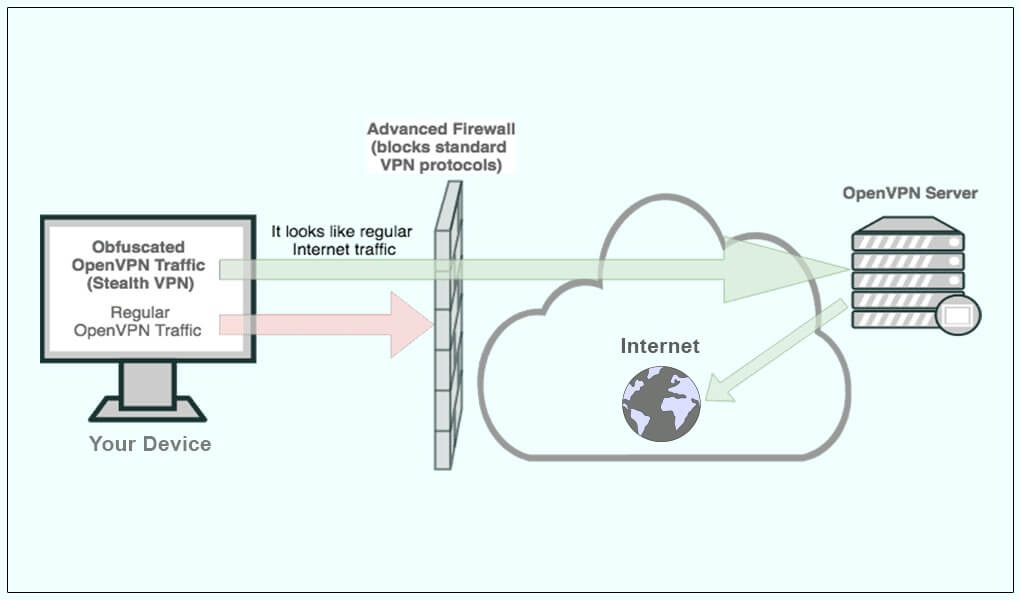
All of these are reasons why you might use a stealth VPN. Stealth VPNs, also sometimes known as “obfuscated” or “camouflaged” VPNs, work by changing the appearance of encrypted traffic to appear as regular Internet traffic.
Because stealth VPN traffic appears identical to normal, unencrypted Internet traffic, it cannot be detected by firewalls, even those using deep packet inspection. This makes it far more secure and an ideal option for those looking for the highest level of online privacy.
How a ‘Stealth’ VPN Works
There are a number of different VPN obfuscation protocols, but generally, stealth VPNs work by modifying your device’s data packets and stripping away information that identifies the packets as originating from a VPN.
VPN data packets generally contain a header, which has to identify information, as well as an encrypted section that contains the actual relevant data. During the obfuscation process, the VPN metadata is removed from the header.
After the VPN data is removed, the data packet is disguised as HTTPS web traffic, the same protocol used by ordinary web traffic. This makes it identical in appearance to regular data packets and thus virtually undetectable by VPN-blocking firewalls.
When to Use a Stealth VPN
Stealth VPNs can come in handy in a number of situations.
As mentioned earlier, stealth VPNs are helpful if your school or business network blocks VPN traffic. Since stealth VPNs disguise encrypted traffic as regular HTTPS traffic, your network firewall will be none the wiser.
Even if your network firewall doesn’t block VPNs, it may still be able to detect VPN usage. Using a stealth VPN can still be helpful in this case because it will prevent your VPN activity from being noticed by the network administrator.
Keep in mind that using a VPN on a school or business network may be a violation of its Terms of Service or Acceptable Use Policy.
Stealth VPNs also come in handy if your ISP or network throttles VPN usage for bandwidth conservation reasons. If you’d like to surf the web in privacy without experiencing any slowdowns, an obfuscated VPN is a great option.
Finally, if you’re concerned about privacy, a stealth VPN is the ultimate in online anonymity. Since stealth VPN traffic appears identical to unencrypted HTTPS traffic, using a stealth VPN is a great way to bypass government censorship.
The Best Stealth VPN Providers
When selecting a VPN provider for stealth purposes, keep in mind that many VPNs don’t offer this feature yet. Additionally, some VPNs are better than others when it comes to getting past firewalls.
We recommend NordVPN, ExpressVPN, IPVanish, Surfshark, and Torguard if you’re looking for a high-quality Stealth VPN. They all offer robust obfuscation modes as well as fast performance and a bevy of other features for anonymous online protection.
If you’re on the lookout for a stealth VPN provider, make sure it also offers strong protection against IP leaks. IP leaks can compromise your real IP address to your network or ISP, undermining your online anonymity. Good-quality VPNs will protect you against leaks.
Finally, make sure your chosen VPN provider offers a killswitch feature. A VPN killswitch will automatically turn off your Internet connection if you are disconnected from the VPN. This will prevent you from being exposed should your VPN connection go down for any reason.
Stealth VPNs: The Bottom Line
As VPNs become more popular, firewall technology continues to evolve to catch up. New methods are being developed to make it more difficult for people to stay anonymous online, so ordinary VPNs may not be enough to protect you in some cases.
Stealth VPNs are a solution for this. By using a stealth VPN, you can bypass VPN-blocking firewalls and give yourself an added layer of privacy when you use the Internet.